

Hardware Wallets - How to Store Bitcoin and Other Cryptocurrencies Safely?
With great power comes great responsibility. One of the main advantages of cryptocurrencies is that, despite their digital form, you own and manage them entirely yourself. Unlike the digital form of traditional money, you don't have to rely on any third party to entrust it to. However, this very advantage carries with it a great responsibility for cryptocurrency users. How can you store and manage your cryptocurrencies, or more precisely the keys to them, securely? That's what you'll find out in this in this article.
Hardware Wallets (EVERYTHING YOU WANT TO KNOW) - CONTENTS:
- Hardware Wallet: Key Chain for Your Private Keys
- Exchange vs. Crypto Wallet - No Private Keys, No Coins
- Paper Wallet — an Analogue Alternative to HW Wallet
- Software Wallets - Almost as Secure as Hardware Wallets?
- What Is a Hardware Wallet?
- What Are Hardware Wallets Good For?
- How Does the HW Wallet Work and What Can It Do?
- Hardware Wallet Trezor One
- Hardware Wallet Trezor Model T
- Ledger Hardware Wallet
- KeepKey Hardware Wallet
- Are Hardware Wallets Really Secure?
- Compromised HW Wallet Purchase
Hardware Wallet: Key Chain for Your Private Keys
To claim that you actually have the cryptocurrencies in your possession is a bit misleading. You don't actually physically own any unit. You only own the key that entitles you to use these cryptocurrencies. Of course, we are talking about a cryptographic key, not a physical key. Without sounding too strange, let's take a layman's look at the cryptography behind cryptocurrency wallets.Asymmetric Cryptography
Asymmetric cryptography is one of the most important inventions of the last century. Have you heard of it? It's all around you.
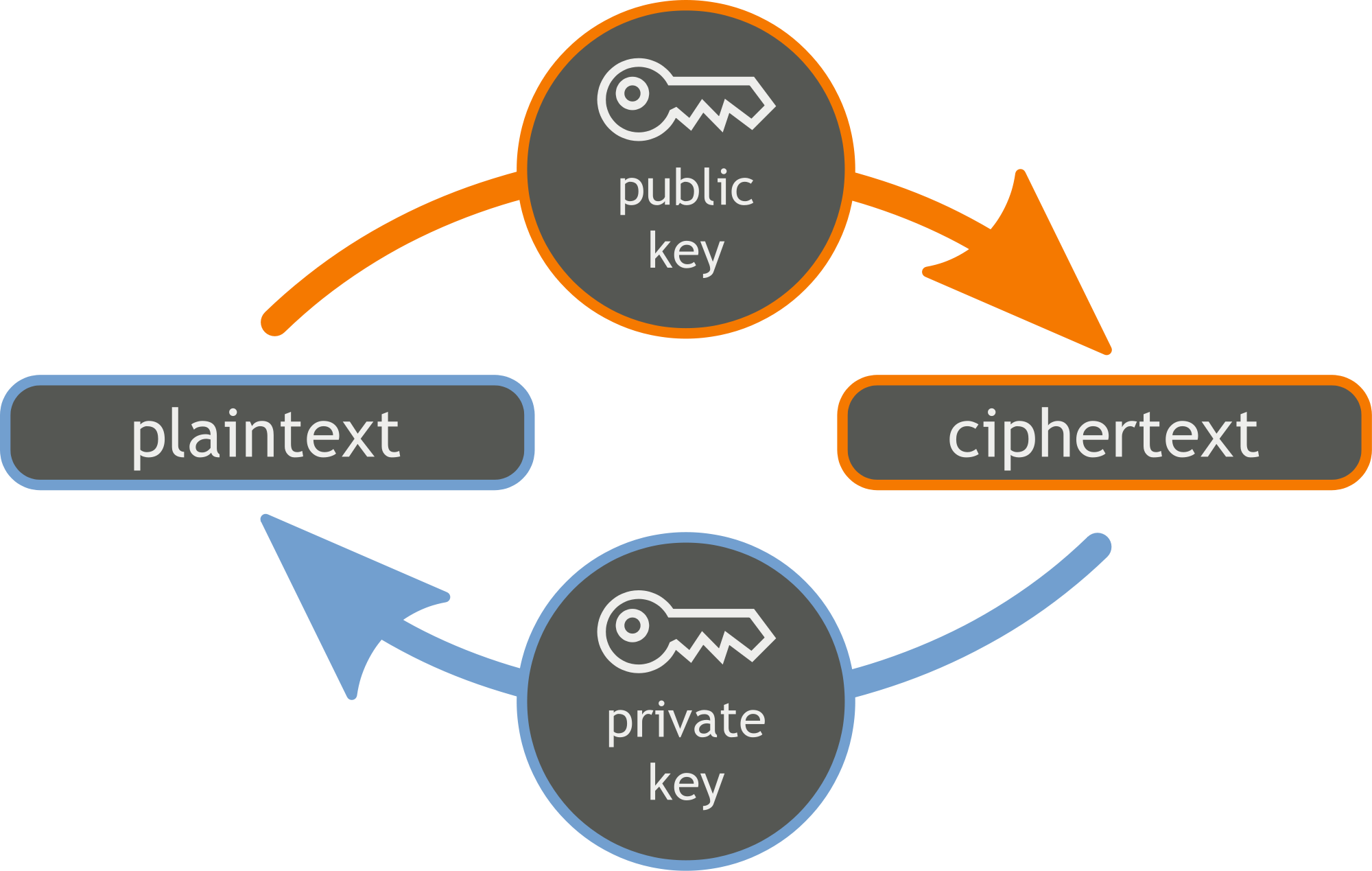
For centuries of human history, you've needed one key to encrypt messages. The other party who received the message then needed the same key to decrypt it. Asymmetric cryptography, which yields two keys, changes this. Let's call them public and private. If I encrypt something with my public key, I can only decrypt it with my private key. You can think of it as a padlock, which you can lock but not open without the key. The keys are complementary, but I can't decrypt one without the other.
This principle works everywhere in computer science. If you are reading this article and you are connected to it via https, your computer has exchanged a few keys with the server and is communicating encrypted. So where does the "crypto" in cryptocurrency come from? How does the transaction work? Cryptocurrency, as the name makes clear, is built on cryptographic principles.
Transactions
We can observe the principle of public and private keys on the bitcoin wallet. Your address in the wallet represents the public key. Of course, the private key corresponds to it. This authorizes you to spend cryptocurrency at your address. A little more math and cryptography later - in short, you need your private key to send a transaction. You sign the transaction when you send it, and this signature is sent to the network along with other transaction data. So, thanks to the mathematical relationship between the keys, nodes on the network can verify that the signature of this private key matches the public key - your address.
Public key signature authentication is an important use of asymmetric cryptography. This verification is provided by non-deceptive mathematics. The private, private or signature key is the essential detail that allows you to own cryptocurrencies or send them in transactions. The hardware wallet we're going to talk about today, then, is a secure keychain for your private keys. Each person is responsible for their own private key. So what are the ways I can save it?
i
A Peer-to-Peer Electronic Cash System, the name Bitcoin whitepaper is no coincidence. Cryptocurrencies like Bitcoin represent the first form of digital cache. Until its inception, all forms of digital money were managed by a third party. In order to trade online, you needed a bank, PayPal, Visa, etc. Bitcoin is the first form of digital asset that you can send without the need for a third party, i.e. peer-to-peer. You actually have it with you and don't need to store it using a third-party system. This is one of the primary benefits of cryptocurrencies.
Exchange vs. Crypto Wallet - No Private Keys, No Coins
Before we get into explaining actual crypto wallets, I can't help but mention exchanges. These are the least secure way to store cryptocurrencies. By leaving your cryptocurrencies on an exchange, you are depriving yourself of the aforementioned advantage of cryptocurrencies as a digital cache. The private key to cryptocurrencies on the exchange is not owned by you, but by the exchange itself. It's a third party you have to trust.
Many users leave cryptocurrencies lying around on the exchange after exchanging money, rather than sending them to their own, e.g. hardware, wallet. Stock exchanges are very often the target of hackers' attacks. People lose money and cryptocurrencies lose reputation. The rule of thumb is that when you are not actively trading cryptocurrency, you need to store it in your own crypto wallet. Such a hardware wallet, for example, is an almost unsolvable problem for remote hackers. It's these real wallets that we're looking at in today's article.

Andreas M. Antonopoulos
>Andreas M. Antonopoulos je jeden z najznámejších propagátorov Bitcoinu, kryptomien a decentralizácie. Je expert v oblasti bezpečnosti a distribuovaných systémov, píše a prednáša na tieto témy. Je autorom kníh Mastering Bitcoin, The Internet of Money 1, 2 a Mastering Ethereum.
Paper Wallet - Analogue Alternative to HW Wallet
Let's start with the simplest, a paper crypto wallet. All you really need is a piece of paper to use cryptocurrencies. It has its advantages and disadvantages.

The way it works is fairly simple. Just print out the public and private keys. I can send cryptocurrencies to the public key - the address - and use the private key to pay for them or withdraw them from there. A paper crypto wallet undoubtedly has several advantages. It's simple - I don't need any equipment, I don't need to install anything. I can also exchange or sell such paper representations of Bitcoin completely offline. But that doesn't mean that all this is safe.
On the one hand, no one can remotely hack my paper. Analog, paper, hidden under the mattress. That's an air gap that no hacker can fix. On the other hand, I need to generate and print this wallet securely. Here come the disadvantages. The first problem is with the actual printing of the paper wallet. You must print it from a trusted source that does not store your private key in any way. When printing at home, a secure Linux environment is recommended.
However, the payment itself is also a big problem. When I want to pay for a coffee, for example, with the crypto wallet in the picture, I have to show my private key to the payment terminal. So I have to trust another party that they will take only what they are entitled to. The safety is of such approach is therefore questionable. At the same time, anyone can take a picture or scan this private key and deprive me of all my deposited money. A hardware wallet, on the other hand, is secure in this sense. Private keys are password protected. Plus, if it burns, gets lost, or is stolen, you can recover it and with it, your cryptocurrencies. But more on that in a moment.
Software Wallets - Almost as Secure as Hardware Wallets?
Mobile and desktop wallets, which are basically apps on your mobile or computer, bring many features that paper wallets cannot have. You can, for example, manage your wallet, keep track of transactions, set fees. Each offers different benefits and focuses on different functions. Of course, many also allow various special transactions and, crucially, open channels and send transactions via the Lightning Network.
They also increase anonymity and security. Anonymity is enhanced by a "hierarchical deterministic" wallet. This is a function that generates an additional address with each payment. Unlike a paper wallet, all transactions do not go through one address and are less trackable.
Various wallet features also allow you to work with cryptocurrencies more anonymously. For example, Samourai or Wasabi, if you are a desktop user, focus specifically on anonymity-enhancing features such as CoinJoin or torification.
Mobile wallets are therefore more practical and anonymous. But are they also safer? Unlike paper keys, the private key is encrypted on your device. Although the app itself treats the private key securely, your device is still online and vulnerable. Security depends on the type of device, the operating system and, last but not least, your security habits.
I generally say that I wouldn't keep more money in my software wallet than I would take in my physical to town. So where do I put the money that I'm saving up? Enter hardware wallets, with the benefits of both of the aforementioned worlds.
What Is a Hardware Wallet?
It is a standalone device with its own hardware, specially designed and intended to store private keys. It's usually about the size of a USB flash drive. But it's not just some secure USB drive — it hides a little computer inside. The computer has a processor, memory, display, buttons and an interface. Yet it maintains maximum simplicity of design. A single-purpose computer that keeps the private key securely encrypted and offline.
Simplicity is a strong security advantage in this case. The more complex the system or device, the more prone it is to have weaknesses. It combines all of the previously mentioned advantages and possibilities that software wallets offer, but also the security of an offline paper wallet.
i
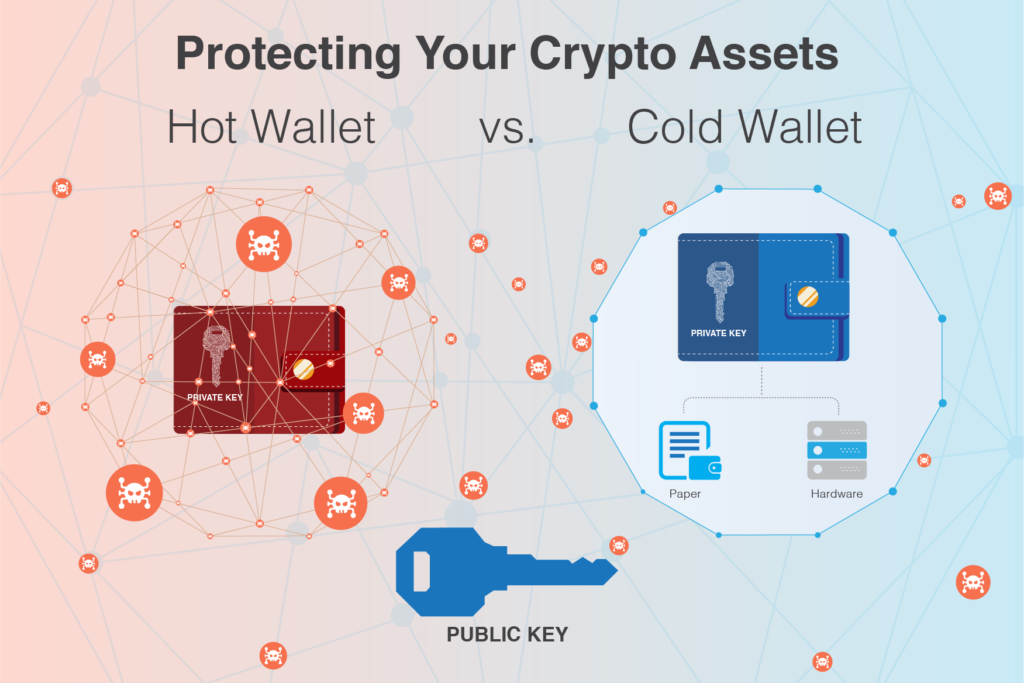
I've used the term offline a few times when talking about holding a private key outside of a device with an internet or mobile network connection. In this respect, the terms "hot wallet" and "cold wallet" is more commonly used. A hot wallet is a wallet that is connected to the internet and you actively work with it. That is, the one on your mobile phone or computer. Cold wallet, on the other hand, is the one that stays offline. So paper wallet or hw wallet.
What Are Hardware Wallets Good For?
A hardware wallet is a physical wallet for cryptocurrencies that brings a new level of security. The private key is stored in the encrypted part of the microcontroller and we cannot transfer it in plaintext. Since it's a standalone device without a system, it's immune to malware and viruses, which are a problem for software wallets. You can use it on virtually any computer without having to worry about any security breaches. That's what hardware wallets are designed for.
In theory, you can use them on any device and not worry about your cryptocurrency being stolen. Private keys never come into contact with potentially dangerous software. So if you want to hold a sum of money in cryptocurrencies that you don't want to lose, and manage it efficiently, a hardware wallet is the best choice. It's safe to say that hardware wallets are the safest way to store cryptocurrencies.
i
The security model of hardware wallets works with the zero trust principle. Their security philosophy is based on the fact that the device you use to manage your wallet may not be secure. You can use it even if your computer is infected with malware and still not worry about losing your cryptocurrency.
So how do hardware wallets work and what features ensure their security?
How Does the HW Wallet Work and What Can It Do?
The first time the wallet is initialized, a seed is generated. This is nothing new compared to software wallets. But wait a minute, did you say "seed?" Let me introduce it to you.
Seed
The hardware wallet will show you the seed you write down on paper when you first turn it on. This seed represents several words, usually 24 or 12. We can say that these words represent your private key and therefore serve as a backup. If your hardware wallet gets lost, broken or stolen, you can enter these words into your new device and you won't lose any money.
On the other hand, if someone gets hold of those words, they can steal all the cryptocurrencies from that wallet. Therefore, it is not recommended to store your seeds digitally under any circumstances. Every device is potentially vulnerable, but no one has hacked the paper yet. I have already hinted at a similar principle above with the paper wallet.
If you are still worried that your house will burn down even with a paper backup, there are ways to save the seed in a form resistant to the last apocalypse, the so-called. Cryptosteel. Here we can observe the first advantage of hardware wallets. The generated seed is shown to you by the wallet itself, a secure environment. This is a clear security advantage over software wallets. A potential hacker watching your computer screen won't know anything.

PIN
Similarly, the PIN that you use to log into the hardware wallet. You enter it either directly on the wallet or on the computer screen, as Trezor (Vault) does. It only shows you 9 blank buttons on your computer and you can see the key layout in the Vault itself. This distribution is always random. So if a hacker is watching your screen or has installed a keylogger on your computer, again, they won't be able to eavesdrop on you.

Passphrase
Another security feature of hardware wallets is the passphrase, a security phrase. It can help you achieve an even better level of security. A passport is required whenever you try to unlock your wallet. But it is no ordinary password. It brings a much deeper level of security. Passphrase becomes part of your seed.
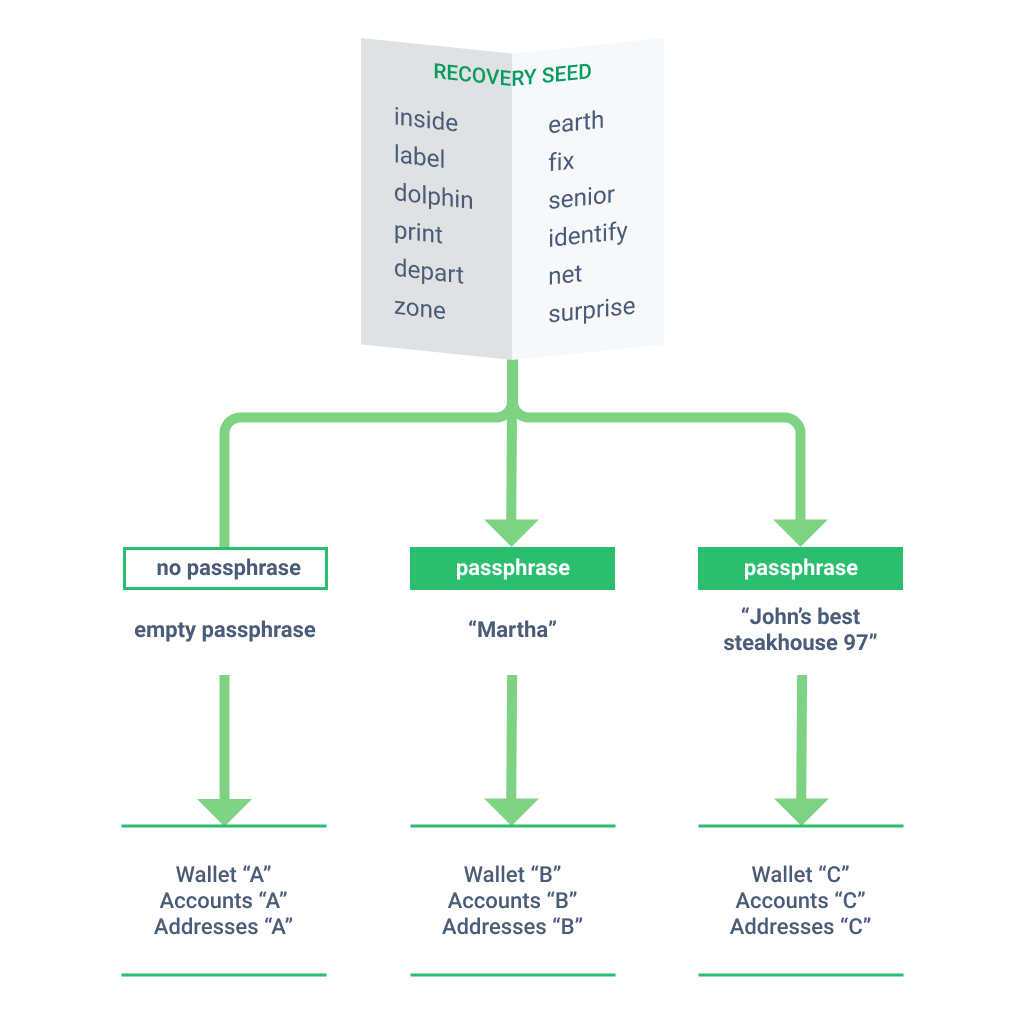
Passphrase is added as a so-called "salt" to the input of the mathematical function that generates the wallet from the seed. This means that if — God forbid — an attacker gets your seed, they won't be able to get to the money through the passsphrase. This property also implies that each new passphrase will generate a new crypto wallet. So you can create as many wallets as you want. In addition to being able to manage multiple accounts in this way, you also get plausible deniability. If you were forced to unlock your wallet, you could use a passphrase that secures either nothing or just a fraction of your portfolio.
Trusted Display
The display of the hardware wallet is where everything important happens. It confirms transactions, checks addresses, displays your seed. The display of the wallet itself must therefore be completely trustworthy. This is what we call a trusted display.
The display is an isolated environment that is constantly offline. Its architecture is open-source, so we can consider the display as trustworthy and as the only source of truth. In case your device was hacked, the display will always show what is really going on and thus is the most important failsafe element of your hardware wallet.
There are many ways hardware wallets use to provide security for your cryptocurrencies and though these vary from wallet to wallet, one feature is the common denominator you can expect every hardware wallet to have: an encrypted private key stored offline in a simple device. Now, which hardware wallet is the best choice? Let's take a closer look at each wallet that the hardware wallet market has in store.
Hardware Wallet Trezor One
First, we will take a look at the oldest and probably the most widespread hw wallets in Europe: Trezor ONE Black and Trezor ONE White by SatoshiLabs — it's simply a classic.

By definition, the Trezor fits everything described above. As I outlined by its name, it generates the private keys itself and never leaves it. They are therefore not accessible to any malware. It uses a deterministic wallet structure, so it can hold an unlimited number of keys using a single seed.
Trezor One has introduced a unique way to enter your PIN that protects you from keyloggers. But it also offers additional protection in the form of a security phrase. You can even use several of them at once to achieve plausible deniability.
I mention the safe first also because it is the oldest hardware wallet ever. Its creators, Slush and Stick, are the inventors of the concept of hardware wallets. In 2011 they started working on Trezor and shortly after, in 2013, they founded a successful company SatoshiLabs. It is one of the top positions in the cryptocurrency industry held by the Czech Republic. Learn the story behind the creation of the Trezor crypto wallet in this article.
The device itself has two buttons and a black and white display. For each transaction, the address will be displayed on the screen and you can confirm it with the button. It uses a USB interface for communication. Of course, you won't find any Bluetooth or Wi-Fi in it. On a computer, it uses a browser with an extension as the interface for communication. You connect encrypted to a website through which you log into the device and manage your cryptocurrencies. No need to install anything, just connect your Trezor wallet and enter your address. However, it is always necessary to verify that the address you enter is real and not a fake one designed by a hacker!
The Trezor hardware wallet supports hundreds of different cryptocurrencies, which is a guarantee that this hardware wallet is suitable for your entire crypto portfolio. It also acts as a password manager and provides two-factor authentication. It should be noted that this form of 2FA has a security advantage over SMS and mobile app authenticators. Another great advantage is that Trezor is open-source. You can check how it works or build your own. It's a time-tested device with thousands of users and penetration tests. This is probably why it is so popular in the bitcoin community as a bitcoin wallet.
Hardware Wallet Trezor Model T
Trezor Model T is the new premium version of the Trezor wallet. The new model brings new features that the classic first-generation safe did not have. The Trezor Model T comes with a colour touchscreen, SD card slot, new design, USB-C, and many other features.

Thanks to the touchscreen, you can enter your PIN and security phrase (passphrase) directly on the device. The Trezor Model T has a trusted display feature that you can always rely on for security. Like the previous model, Trezor One, it supports hundreds of cryptocurrencies, has a password manager, and two-factor authentication. This should make it even safer than its predecessor. A simple user interface on a colour display gives hardware wallets a new dimension. If you want to invest in a modern and advanced hw wallet, the Trezor Model T is the right choice.
Ledger Hardware Wallet
Ledger Nano S is also one of the most widely used hardware wallets. Like the Trezor, it has two buttons and a display. However, the main difference is in entering the PIN or seed. The whole thing takes place directly on the equipment. Use the two buttons to select and confirm numbers or letters. Clicking two buttons can be more tedious than on a computer, but this solution is safe and simple. Again, there is no way for a hacker on a computer to get to the PIN on the device. In addition to the PIN, it also supports passphrase. You enter it directly on the device. It can be tied to a secondary or a temporary PIN.

Similar to the Trezor, it connects to the computer via USB, but its interface is different. It uses the Ledger Live app to communicate, which needs to be downloaded, installed and regularly updated. In it, you create a wallet by installing it as an app on your device. The Ledger Nano S has space for 3 to 18 such applications depending on their size. The important thing is that these applications are open-source. It supports more than a thousand different cryptocurrencies. If you don't like Ledger Live, you can also manage Nano S using other apps, such as Wasabi Wallet. You can also use it on Android, unfortunately, iOS does not support it.
Ledger Nano X is Ledger's new and improved successor to the classic S version. It brings some significant changes. The main difference is in the connectivity functionality - it has Bluetooth and its own battery. This makes it more mobile and practical to use. You can easily use the wallet on your mobile phone, but unfortunately, it only supports Android. Nano X easily connects wirelessly to both Android and iOS. It also supports the new USB-C standard and has more capacity for apps. It should hold up to 100 of them. Like the Ledger Nano S, it has a two-button display, but in a new design. Ledger Nano X also introduces a new generation of mobile wallets that come with new features.

KeepKey Hardware Wallet
KeepKey is a hardware wallet from ShapeShift. It combines many of the features mentioned above and is most similar to Trezor in terms of functionality.

Similarly to Trezor One, it uses, for example, an interface, a web browser and PIN entry on a computer with a blind keyboard. However, it has a larger display, which may be more convenient for many users. In addition, it has only one button, which is enough to confirm transactions. The KeepKey supports more than 40 cryptocurrencies or tokens.
When interfacing through a browser, you connect to the ShapeShift site, which also allows you to directly trade cryptocurrencies on the exchange. This is the advantage of KeepKey that other hardware wallets do not have.
Are Hardware Wallets Really Secure?
Of course, we can't leave the safest way to store cryptocurrencies without question either. It is important to note that even hardware wallets can be potentially vulnerable. Most often, however, these are user errors, not vulnerabilities in the software or hardware itself. Despite the security features of hw wallets, you need to be careful when using them.
The seed created when generating a cryptocurrency wallet can actually only be stored on paper. When connecting to the wallet management page, you need to verify its authenticity. Ideally, you should bookmark the right page to ensure that the browser always selects the right one. Similarly, when downloading a hardware wallet management application, you need to verify the originality, i.e. the source, or checksum, of the downloaded application. Attacks happen where the hacker mixes up the address when sending a transaction. So you better off double-check the address you are sending cryptocurrencies to against the one displayed on the device.
Probably the most important thing not to neglect when using hardware wallets is updating. Updates that bring the latest security patches are not only necessary for your computer or mobile, but also for your hardware wallet. A detailed explanation of how to update and safely use hardware wallets is offered by this article.
If you're worried about more advanced security weaknesses, the project wallet.fail points out potential weaknesses in the design of hardware wallets.
However, one of the most common security threats is a compromised purchasing process.
Compromised HW Wallet Purchase
Never buy a second-hand hardware wallet. The purchase may have been compromised because the attacker may have modified or replaced the device with an unsafe one before selling it. The identical device then pretends to be a normal wallet but immediately steals your keys. You may think that this can happen only to the really foolish ones, but even the government has also inserted backdoors into hardware on more than one occasion.

For this reason, the packaging of the hardware wallet is sealed with tape serving as a seal. Always make sure that the device has not been opened before you. To make sure the device is new, don't buy it from a second-hand shop and prefer trusted dealers.

Mário Havel
Mário is a computer science student who loves freedom and technology. He is the chairman of Slovak Students for Liberty, since its inception he has been a member of the Slovak Parallel Polis. He specializes in cryptotechnology, software development and Austrian economics. He regularly organizes events and lectures on these topics.



